A Remote Access Trojan (RAT) is a type of malware that provides cybercriminals with unauthorized access to the victim’s computer system. These are often disguised as legitimate software or attached to files or links in phishing emails. Once installed, a RAT can cause severe damage by stealing passwords, installing additional malware, and even taking control of the entire system.
In this blog post, we’ll guide you step-by-step on how to get rid of Remote Access Trojan malware from your desktop or laptop. This article aims to provide a comprehensive guide on identifying, removing, and preventing RATs from compromising your computer.
Before diving into the removal process, it’s crucial to understand what a RAT is.
What is a Remote Access Trojan (RAT)?
A Remote Access Trojan (RAT) is a type of malware program that allows an attacker to gain unauthorized access to a victim’s computer. Unlike other types of malware, which may have a specific function like data encryption (as in ransomware) or data theft (as in spyware), a RAT provides the attacker with a “backdoor” into the victim’s system, granting them full control over the computer.
RATs are usually hidden in games, videos, music files, or programs. Once activated, they can enable cybercriminals to do anything they want on your computer remotely. RATs can be acquired or even custom-coded by cybercriminals, and they usually come in three main varieties:
- Remote Administration Tools (RATS)
- Backdoor Exploits
- Trojan Horses
These three kinds of software often collaborate to achieve a singular objective: to seize control of or surveil your computer, which in hacker parlance is known as “the host system.”
How Does a Remote Access Trojan (RAT) Work?
A Remote Access Trojan (RAT) is a particularly insidious type of malware because it allows an attacker to gain unauthorized access to the victim’s computer and potentially take over the system entirely. Here’s a detailed breakdown of how a RAT works:
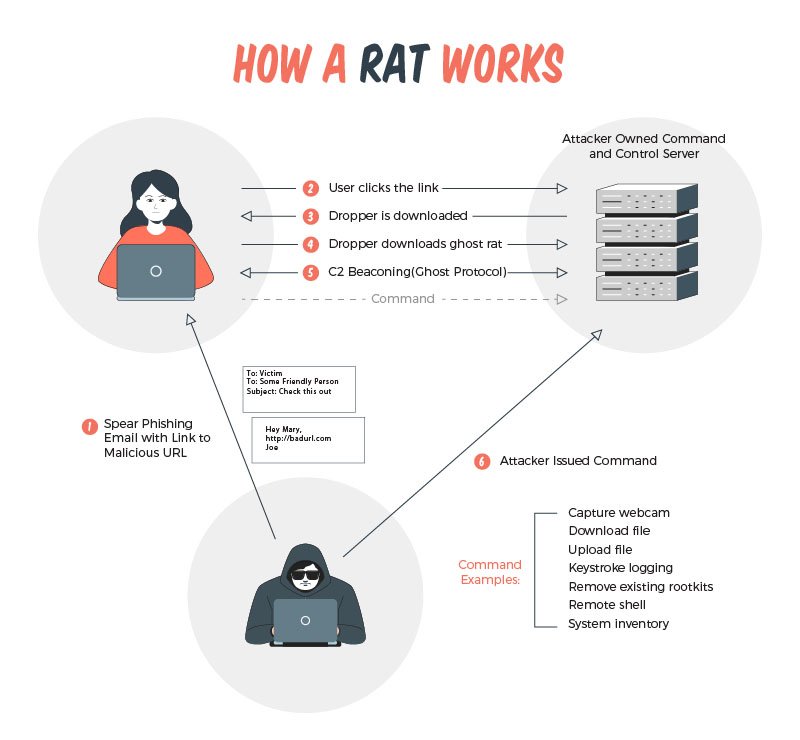
- Infiltration: RATs often infiltrate systems by masquerading as legitimate files or software. They can be attached to emails, embedded in downloadable files, or installed via malicious websites.
- Installation: Once the RAT file is executed on the victim’s computer, it typically installs itself in a way that allows it to start automatically with the operating system. This ensures that the RAT remains active while the computer is on.
- Connection: After installation, the RAT establishes a connection to a server controlled by the attacker. This connection is often encrypted to evade detection by security software.
- Remote Control: Once the connection is established, the attacker can control the infected computer remotely. This can include, but is not limited to, file manipulation, data theft, recording keystrokes, capturing screen images, and even activating hardware like webcams.
- Data Harvesting: The attacker can use the RAT to send data from the victim’s computer back to their own system. This can include sensitive information like usernames, passwords, and credit card numbers.
By understanding how RAT works, you can better appreciate the severity of the threats they pose and the importance of robust cybersecurity measures to detect and remove them.
Symptoms of Remote Access Trojan (RAT) Infection
Here are some signs or symptoms that your computer might be infected with a Remote Access Trojan (RAT) malware:
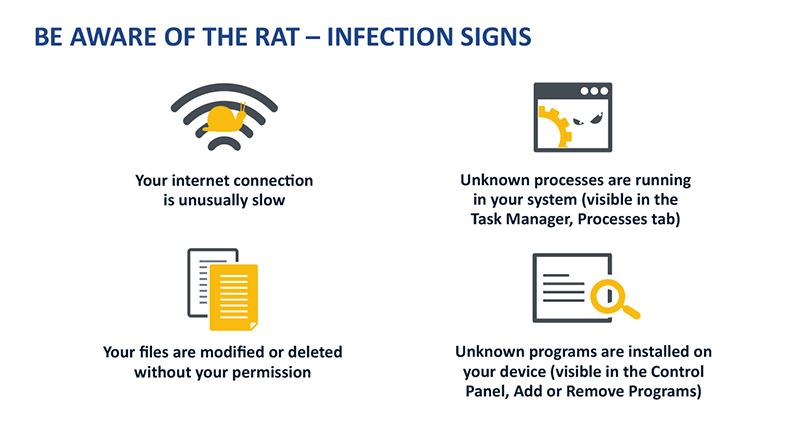
- Sluggish Performance: Unexplained slowdowns could result from a RAT using your system resources.
- Unusual Network Activity: High network usage when you’re not actively using the internet could be a sign.
- Strange Behavior: New, unfamiliar icons on the desktop or unexpected system behavior can be red flags.
- Unauthorized Access: You might be compromised if you notice unknown files or software installations.
Identification Tools: How To Identify Remote Access Trojan (RAT)
Identifying a Remote Access Trojan (RAT) virus can be challenging due to its stealthy nature. However, various tools and methods can help you detect such malware on your system. Here’s a guide on how to identify a RAT:
- Antivirus and Antimalware Software
- Network Monitoring Tools
- System Analysis Tools
- Specialized RAT Detection Tools
- Behavioral Analysis
- Professional Help
1. Antivirus and Antimalware Software
- Full System Scan: Use a reputable antivirus or antimalware program to perform a full system scan. This is often the first and most straightforward step in identifying a RAT.
- Real-Time Protection: Ensure that your antivirus software offers real-time protection, which can detect and block malicious activities as they happen.
- Heuristic Analysis: Some advanced antivirus solutions offer heuristic analysis to detect new, unidentified viruses or malware based on their behavior.
2. Network Monitoring Tools
- Wireshark: This network protocol analyzer can capture and display the data traveling into and out of your computer in real-time. Look for unusual outgoing connections.
- Netstat: This command-line tool displays active network connections. Use it to identify any unfamiliar IP addresses that your computer is communicating with.
- Firewall Logs: Check the logs of your hardware or software firewall for any suspicious outgoing or incoming traffic.
3. System Analysis Tools
- Task Manager: In Windows, the Task Manager can show you all the currently running processes. Look for unfamiliar or suspicious processes that consume a lot of CPU or memory.
- Resource Monitor: This tool provides more detailed information than Task Manager, including which services are associated with each running process.
- Sysinternals Suite: Tools like Process Explorer and Autoruns can provide in-depth information about running processes and startup items.
4. Specialized Remote Access Trojan (RAT) Detection Tools
- GMER: This rootkit detector and remover can identify hidden processes, often a sign of a RAT.
- RAT Decoders: Some specialized tools can decode the configuration settings of known RATs, helping you identify them specifically.
- Online Scanners: Websites like VirusTotal allow you to upload suspicious files for scanning. They use multiple antivirus engines to identify malware, including RATs.
5. Behavioral Analysis
- Unusual System Behavior: Watch for signs like unexplained system slowdown, frequent crashes, or unauthorized changes in system settings.
- Unauthorized Access: If you notice unfamiliar files or software installations or your personal files have been altered without your knowledge, these could be signs of a RAT.
6. Professional Help
- Cybersecurity Firms: In severe cases, or if you’re running a business network, you may need to consult with cybersecurity professionals who can perform a detailed forensic analysis of your system.
Using these tools and methods can improve your chances of identifying a Remote Access Trojan (RAT) on your system. Once identified, the following steps would involve removal and future prevention, which are crucial for maintaining digital security.
RAT Removal Methods: How To Get Rid of Remote Access Trojan (RAT)
Getting rid of a Remote Access Trojan (RAT) from your computer system is a critical task that requires a multi-faceted approach. Here’s a comprehensive guide on how to get rid of a RAT (Remote Access Trojan Horse):
Preliminary Steps
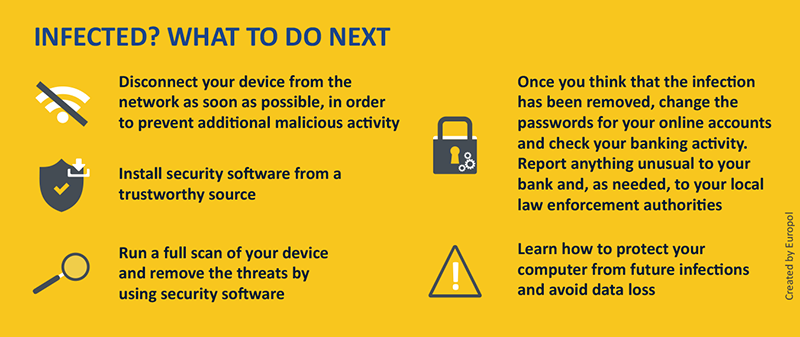
- Disconnect from the Internet: Unplug your computer from the network to prevent the RAT from communicating with the attacker’s server.
- Backup Important Data: Before taking any removal actions, back up essential files to an external drive or cloud storage. Ensure the backup is clean and not infected.
- Safe Mode: Reboot your computer in Safe Mode to disable any non-essential processes and services, making it easier to remove the RAT.
Manual Removal of Remote Access Trojan (RAT)
- Identify Suspicious Processes: Use Task Manager or a specialized tool like Process Explorer to identify any unfamiliar or suspicious processes running on your system.
- Terminate Processes: Right-click on the suspicious process and choose ‘End Process’ or ‘End Task.’
- Locate and Delete Files: Navigate to the file location indicated in the Task Manager or Process Explorer and delete the suspicious files.
- Registry Cleanup: Open the Windows Registry Editor (regedit) and search for entries related to the RAT. Delete them carefully.
- Warning: Editing the registry can be risky. Make sure to back it up first.
Automated Removal of Remote Access Trojan (RAT)
- Full System Scan: Use a reputable antivirus or antimalware program to perform a full system scan. Make sure the software is updated with the latest definitions.
- Quarantine and Delete: Most antivirus software will automatically remove or quarantine the RAT. Follow the software’s instructions to delete the quarantined files.
- System Repair: Some advanced antivirus solutions offer features to repair system files and settings altered by the malware.
Network-Level Measures
- Firewall Rules: Configure your firewall to block outgoing connections to the attacker’s server. Check your firewall logs for any suspicious activity.
- Router Security: Change your router’s admin credentials and update its firmware to the latest version. Some routers have security features that can help block malicious traffic.
Post-Removal Steps After Getting Rid of Remote Access Trojan (RAT)
Follow the below-mentioned post-removal steps after deleting Remote Access Trojan (RAT) from your computer system:
- Change Passwords: After you’ve removed the RAT, change all your passwords, especially for sensitive accounts like email, social media, and banking.
- Software Updates: Ensure that your operating system and all software are up-to-date to minimize vulnerabilities.
- Security Audit: Perform another full system scan to ensure that the RAT and any associated malware are completely removed.
- Monitor for Symptoms: Look for any signs of re-infection and act immediately if you notice anything suspicious.
By following this comprehensive removal guide, you can effectively eliminate a RAT from your system and take steps to prevent future infections. Remember that vigilance and up-to-date security measures are your best defense against cyber threats.
How To Prevent Remote Access Trojan (RAT) Infection
Preventing a Remote Access Trojan (RAT) infection is far better than dealing with the consequences of an attack. Here are some proactive measures you can take to protect your system from RAT infection:
- Software and System Updates
- Network Security
- Email and Web Browsing
- User Behavior and Access Control
- Regular Scans and Monitoring
- Employee Training and Awareness (For Businesses)
- Backup and Recovery
1. Software and System Updates
- Operating System: Keep your operating system updated with the latest security patches. These updates often contain fixes for known vulnerabilities that RATs could exploit.
- Software Updates: Regularly update all software, including your web browser, plugins, and any other applications you use.
- Antivirus Software: Ensure your antivirus software is up-to-date with the latest malware definitions.
2. Network Security
- Firewall: Use a robust firewall to monitor all incoming and outgoing traffic. Configure it to block unauthorized access.
- Secure Wi-Fi: Always use strong, unique passwords for your Wi-Fi network. Enable WPA3 encryption if your router supports it.
- VPN: Use a Virtual Private Network (VPN) when accessing the internet on public networks to encrypt your data and hide your IP address.
3. Email and Web Browsing
- Phishing Awareness: Be cautious with emails from unknown sources. Only click links or download attachments if you know the sender’s identity.
- Secure Browsing: Use HTTPS websites whenever possible. Look for the padlock symbol in the address bar to ensure a secure connection.
- Ad Blockers: Use ad blockers to prevent malicious ads containing RATs from appearing on websites.
4. User Behavior and Access Control
- User Privileges: Use a standard user account for daily activities and an administrator account only when necessary. This limits the potential damage a RAT can do.
- Two-Factor Authentication (2FA): Enable 2FA on all accounts, especially those containing sensitive or personal information.
- Password Management: Use strong, unique passwords for all accounts and store them in a secure password manager.
5. Regular Scans and Monitoring
- Scheduled Scans: Set your antivirus software to perform regular full-system scans.
- Real-Time Monitoring: Use security software that offers real-time monitoring to detect and block malicious activities as they happen.
- Network Monitoring: Use network monitoring tools to monitor all devices connected to your network and the data traffic they generate.
6. Employee Training and Awareness (For Businesses)
- Security Training: Educate employees about the risks of RATs and other malware and train them to recognize phishing attempts.
- Access Control: Limit employee access to sensitive information and use monitoring software to track who accesses what.
- Incident Response Plan: Have a well-documented and rehearsed incident response plan in case of a RAT or other malware infection.
7. Backup and Recovery
- Regular Backups: Regularly back up important data to an external drive or a secure cloud service.
- Recovery Plan: Have a disaster recovery plan in place to quickly restore your system to a clean state in case of an infection.
Implementing these preventive measures can significantly reduce the risk of a RAT infection. Remember that cybersecurity is ongoing; staying updated on the latest threats and security best practices is crucial.
Conclusion
Remote Access Trojans (RATs) are a severe threat that can compromise your data and privacy. However, with the right tools and practices, you can effectively remove and prevent them. Always stay vigilant, update your software, and practice safe browsing habits to minimize risks.
By following this comprehensive guide, you’ll be able to get rid of the Remote Access Trojan (RAT) from your system and prevent future infections. Stay safe online!
You Might Also Read:
- Best Ways To Secure Your Online Identity
- What A VPN Can Do When You Browse Online
- Ways To Check Websites For Viruses and Malware
- How To Stay Private on the Internet

Be the first to comment